
Local government leaders serve their communities as orchestral conductors of policy and planning. This role harmonizes stakeholders, policies, processes, and divergent interests in pursuit of that pure sound of sustainable cities for the future. Alongside the harmonizing nature of management, however, is the risk management task of protection of assets. Here we focus on the risks associated with developing ever “smarter” cities. We are particularly concerned with addressing city-wide cybersecurity risks encountered in an integrated smart city, namely vulnerability to cyberterrorism. Intelligent technologies for cities are an empowering dream; we can utilize actionable data to improve traffic, lighting, water maintenance, and efficiently control power grids. At the same time, all these advances require vigilance to the highest standards of cyber protection against increasingly porous attack surfaces in delivery of smart services. Local leaders and their teams need continuing education on best practices to ensure well-designed and risk-minimizing practices that are sustainable with dynamic security risks facing smart cities.
Could cyberterrorism happen in your city? Suppose all your files are locked and your city operations come to a screeching halt. Cyber lockdown could be worse than any COVID-19 quarantine. If access to services and everything digital within the city is locked, the city and its constituents are assaulted with fear—the terrorist’s weapon. Or worse, your water supply or traffic or emergency services could be compromised and lives lost on an unimagined scale. Even if you resolve the event, it can and often does happen again. Why? Because smart city attack surfaces evolve like viruses and offer multidimensional opportunities for hostile cyber actors. Indeed, this could lead to you or your fellow leaders being dealt an “RGE.” In cyber speak, an RGE is a “resume generating event,” meaning you were terminated. Urban cyberterrorism can and does happen to cities regardless of their size. For city managers, this article focuses on risk management as the “what” and a subsequent article in the July issue focuses on digitally driven automation as the “how” to lead a cybersecurity “identify, defend, detect, respond, recover” cultural transformation along the smart city journey.
Urban Cyberterrorism: Opportunistic, Not Selective
Hostile cyber actors (the bad guys/hackers/for cities, often nation-state sponsored and well-funded) are looking for and finding vulnerabilities in a city’s digital and physical ecosystem. Your city’s weakest link and vulnerabilities make you a potential next victim. These attacks are sophisticated and automated; the intent is to sow fear, distrust, and terror to debilitate a city, or even a nation. Ransomware (one form of attack) is an easy form of extortion. Any breach is very costly to your city, even if you pay the ransom. Smart city risk management is required to avoid becoming that next victim. You must understand, however, that no magic pill, no panacea exists in a zero-trust ecosystem1 that evolves dynamically at computer-mediated speeds. No single new technology or quick fix is enough. Diligent and far-sighted risk management is the only antidote. New models are required for risk management that look at sensor-generated telemetry, multidimensional data used to spawn intelligence about threats, and vulnerability risk estimations. The National Institute of Standards and Technologies (NIST) suggests the following:
Assume that an attacker is present on the network and that a city-owned network infrastructure is no different—or no more trustworthy—than any non-city-owned network. In this new paradigm, a city must continually analyze and evaluate the risks to its internal assets and business functions and then enact protections to mitigate these risks.”2
Protective urban cybersecurity is led by the city manager. Smart city cyber-related risks have consequences. Today these consequences are measured in dollars, losses, lives, and risks for which you as manager are accountable. Bad actors are often well financed and staffed, while cities struggle with overextended services and budget constraints. How should managers then proceed in the face of the complexity of smart city technologies?
A 2019 New York Times article highlights cities both big and small that are increasingly the target of hostile cyber actors.3 Many cities think they are too small to worry about such things, or that their firewall and antivirus software protect and secure them. The reality is that urban cyberterrorism is opportunistic, and every city is a potential target as it pursues intelligent city services as a smart city.
Key Cybersecurity Dimensions
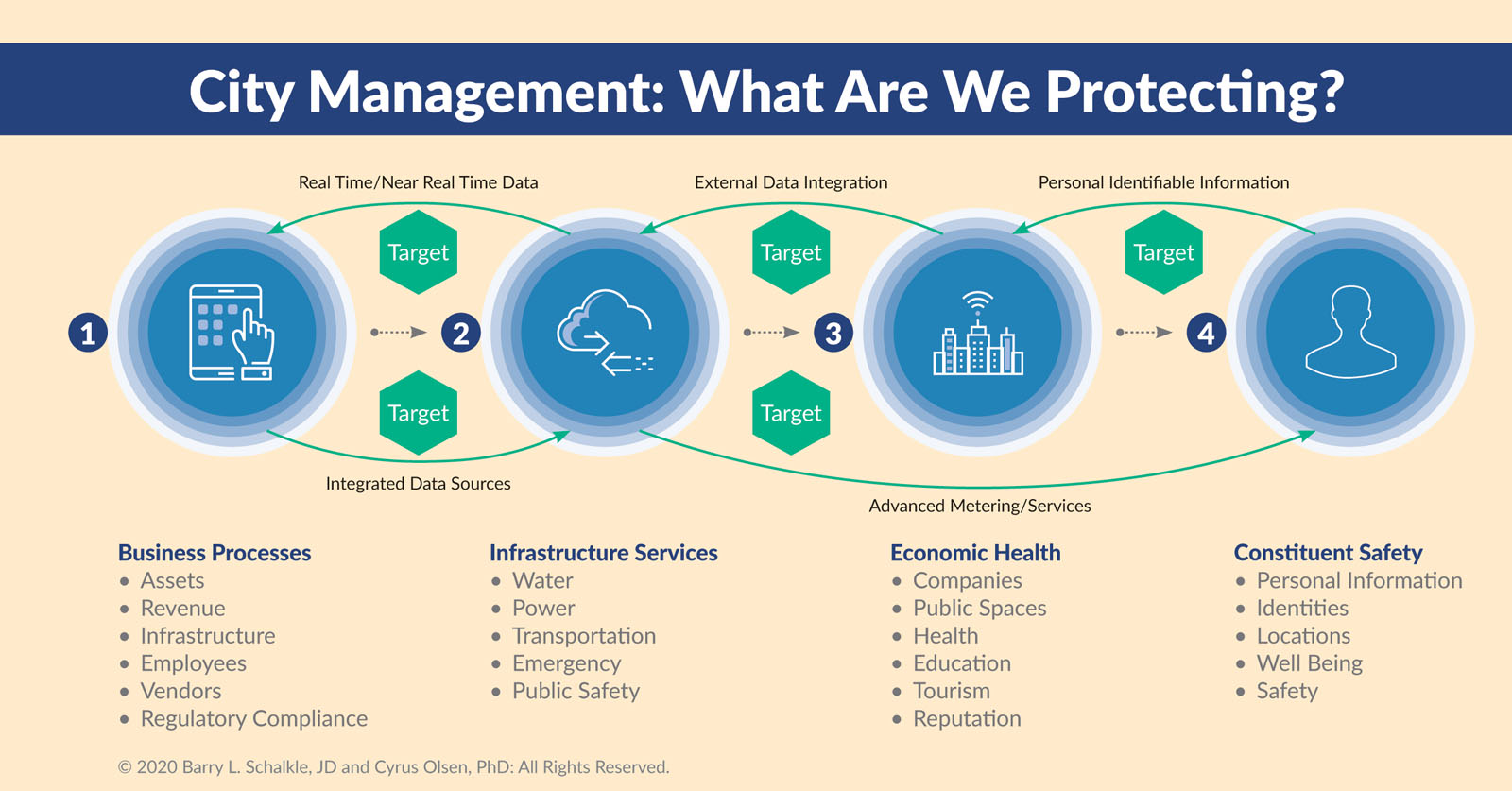
Smarter city ecosystems have four key cybersecurity dimensions forming an increasingly porous attack surface. These dimensions change dynamically as smart city technologies are implemented:
1. Business Processes: Assets, revenue, infrastructure, employees, vendors, and regulatory compliance.
2. Infrastructure Services: Water, power, transportation, emergency services, and public safety.
3. Economic Health: Economic wellness of companies, health, education, tourism, and reputation.
4. Constituent Safety: Personal information, identities, location, and safety.
These interdependent dimensions and attack surfaces grow as smart city infrastructures mature, which means the monolithic defense-in-depth approach, owned by IT, is no longer possible or advisable. The reality is that smart cities require diverse data flowing across technical and organizational boundaries. These data elements need to be integrated at machine speeds with threat responses automated in near real time to mitigate threats in the operational infrastructures like water, transportation, and power grids. For a city manager, a new way of viewing cybersecurity is required.
According to research:
Small municipalities are particularly vulnerable, as nearly half of attacked cities in 2019 had a population of 50,000 people or less. The analysis also found that two-thirds of ransomware attacks in 2019 were aimed at government organizations.4
Cybersecurity ignorance can result in a city-wide failure in an interconnected city using smart technologies.5 Facing a zero-trust world, how does a local government leader manage these risks and perhaps even lagging cybersecurity capabilities?
Cybersecurity: A Risk Management Decision, Not an IT Decision
Risk management is the reduction of uncertainty,6 and the city manager’s role is leadership. Local government leaders are responsible for thought leadership, decision guidance, accountability measurement, resource allocation control, and ensuring uncertainty reduction for all stakeholders over an extended planning horizon. Risk management decisions are themselves risky, especially in the face of concerns about surveillance and personal privacy and with the impact of major events like the COVID-19 pandemic.
To be sure, IT plays a pivotal role since it is the domain of identity and access management in a zero-trust world. But it is the risk created with tightly coupled telemetry and integration of data at rest and in motion across cloud, premise, and operational infrastructures that must be considered in a smart city context. This requires a leadership role at the highest levels to ensure unified, collaborative behaviors throughout the entire city operational infrastructure and organization as a risk management “security curtain.”
Even in corporations the average time to breach detection is 197 days7 and cities often are less invested in tools and skills than most mid- to large-sized companies. General Michael Hayden, former director of NSA/CIA, notes that the citizens of the U.S. face “combat in the information domain” and the fact that “this is not just a cyber threat issue.”8
A local government leader as CEO is not mastering the technology, or doing the work of IT, but rather leading across departments, driving cybersecurity best practice policies, building responsible cultural norms, ensuring IT and other departments are communicating, and making funding allocations to ensure secure sensor infrastructures are available in the operational technologies. They are responsible for risk reduction across this ecosystem.9 Building a cybersecurity first (CSF) culture requires a thoughtful balancing of resource allocations, driving CSF-conscious decisions and orchestration of operations with outside experts using empirical and impactful accountability metrics, not anecdotal assurances that a network perimeter is secure.
You and your city cannot make guesses. To make quality decisions you need facts based on reliable data; facts about cross-departmental cybersecurity capabilities and vulnerabilities. Reliable data is generated by enumerating facts about your own digital and physical ecosystem. It is your locality’s data that is important for building decision models and reducing uncertainty to acceptable and measurable levels. Enumeration data is not easy to obtain, and in many cases is totally absent—but knowing that is progress. Without reliable enumeration data, you cannot build out a clear and comprehensive decision framework for smarter city threat surfaces10 like cloud services, internet of things (IOT), industrial internet of things (IIOT), and digital integration. Cybersecurity first (CSF) as a cultural norm is not a subjective risk matrix, used as a heuristic (subjective guessing or “trust me tricks”) for hopeful cybersecurity decisions about IT infrastructure upgrades.
Local government staff need a clear vision of smarter and secure community from their leader. Generating that clear vision requires first building your CSF master plan and a reliable fact-based roadmap. Tight linkages to execution disciplines will increase your probability of success. Without this type of plan, your community could become the next urban cyberterrorism victim, regardless of size.
Challenges of Leading a CSF Culture within Local Government
Experts predict a global shortage of 4.07 million cybersecurity professionals in the year 2020.11 In addition, city/county managers are generally not cybersecurity experts and are often at the mercy of their IT engineers. It becomes a daunting task knowing where to start. How does a thoughtful manager lead the smarter city ecosystem in building that CSF master plan and still do their day job?
Migration to a CSF ecosystem requires digital, operational, and organizational transformations. A local government leader must look at People, Organizational Structure, and Policies and procedures, integrating with Technologies (both current and future), Operational planning, and Projects (current and future) across all departments and stakeholders (POP TOP).12 This POP TOP™ method builds a collaborative roadmap that all stakeholders climbing the smart cities mountain together can forge into a CSF culture.
Guiding a Reasoned Assessment toward CSF Smarter City Ecosystems
Thoughtful transformation of an entire city ecosystem into a CSF community strongly depends on its leadership. For the leader, however, the critical skill lies in generating followers, then enabling transformative change to create cultural norms, vocabulary, and behaviors. This often requires creating a change management role reporting to the chief administrative officer, empowered to enable cybersecurity priorities for departmental leadership and operational planning.13 Following are three cybersecurity leadership tasks:
1. Establishing Your City’s Security Vision
“Visioning” sometimes conjures images of wasted time and unused documents in the face of operational realities, but it remains a critical exercise in any smarter city journey. The value of visioning lies in generation of vision vectors guiding stakeholders toward a culture of security-mindedness and behavior.14 There are critical components to crafting correct vision vectors as directional guiding principles, with both magnitude and direction, embedded in a matrix of interests and anchored to a time frame.
First, vision vectors need enumerated facts establishing a baseline. This requires a comprehensive cyber assessment, including things like the use of collaborative technologies like Zoom under pandemic scenarios. Let’s be clear, a comprehensive cyber assessment is not a self-assessment, nor is it a check-the-box questionnaire. A proper smart city cybersecurity assessment is a thorough third-party analysis of all aspects of your digital ecosystem and its potential for risk. It is not a solution looking for a problem, nor is it a set of technical recommendations. It is not merely a network penetration test by white hat hackers. It needs to cover three critical domains across present state security capabilities guiding smarter city future investments and technological evolution:
• Digital Infrastructure: Including IT, OT (operational technologies, analytics platforms, cloud, hybrid, and physical security, also integrations with external vendors and partners.
• Security Policies: Both organizational policies and digitally automated policies (like access and identity) and associated standards with procedures clarified in understandable language
• Ecosystem Integration Points: Vendors, constituents, other federal and city entities, businesses, and your own organization.
Secondly, it should be an ongoing line item in city budgets. Cybersecurity assessment is a city’s annual cyber risk physical that prevents you from being “sickened” by new and evolving threats.
2. Building Your Roadmap and Beginning Your Evaluation
Once you have a vision clearly defined through thoughtful enumeration, you begin building your roadmap and engage in fact-based evaluation of a department’s current state. You evaluate present state capabilities and identify smarter city aspirations and immediate risk holes to be plugged across the ecosystem.15 This suggests cyber-responsible roles in each department, with responsibilities for cross departmental communications, data quality, and policy compliance.
3. Moving Forward
Once you have completed an assessment and finished the evaluation, you are ready for remediation planning with execution road map detail. The execution roadmap identifies where your city goals and risks are today, specifies acceptable risk levels, and defines roadmap detail balancing capability maturity and fiscal limitations rolling across the time horizon for deployment.
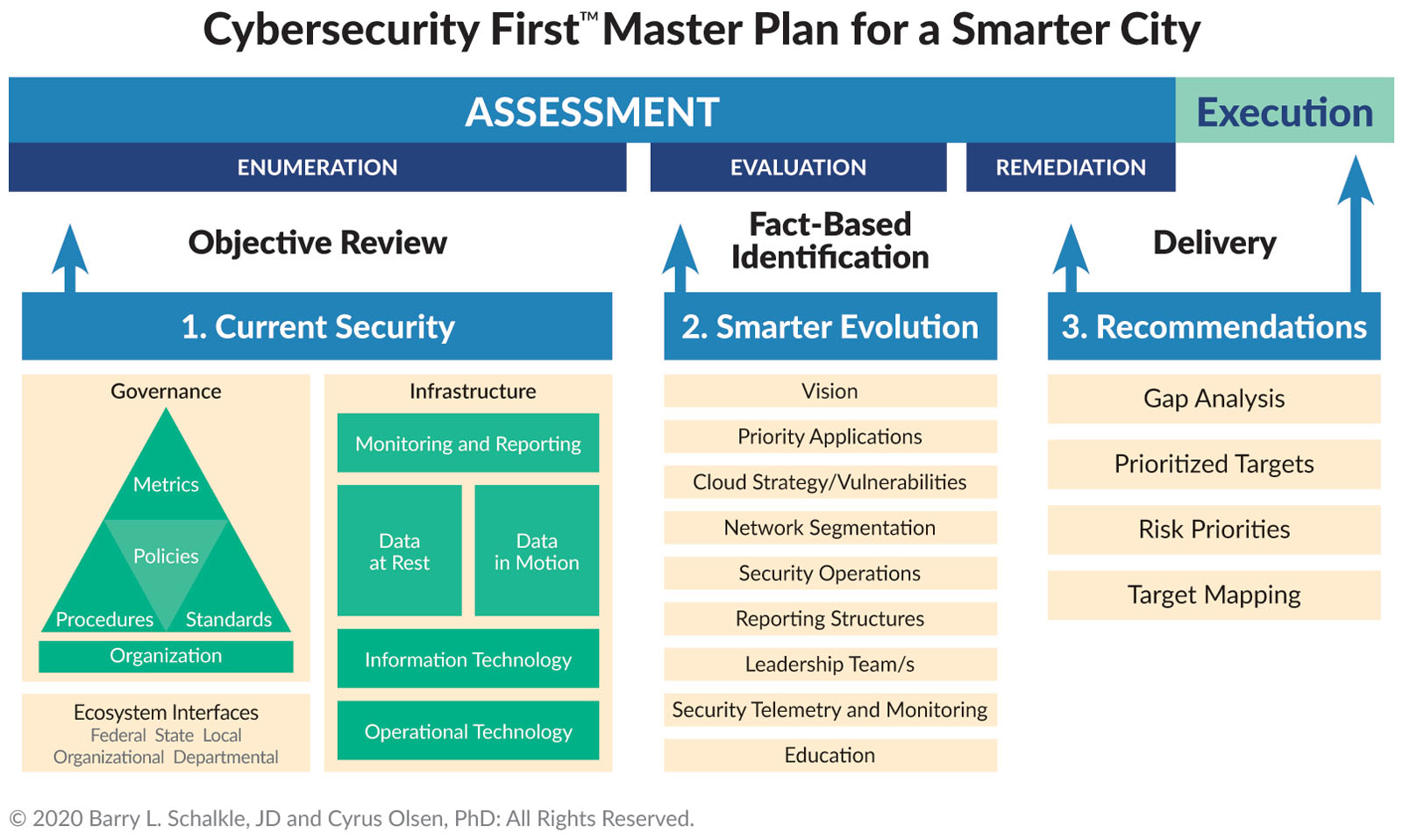
Methodology for Developing Your Security Master Plan
Developing a CSF master plan can be daunting. It is not for the uncommitted and is likely will require third-party experts helping you. The initial assessment establishes your priorities as they relate to your most vulnerable cyber risks and your end-state vision. From there, you establish timelines and resource allocation mapping for both fiscal and leadership needs. Within resource allocation parameters, you will want to make sure that cybersecurity is reporting to the chief administrative officer.16 You want to make sure clear metrics have been established and impactful departmental accountability is in place to ensure tasks and timelines are met.
Combatting cyberterrorism requires daily monitoring of the entire cyber and physical ecosystems and follow up with actionable remediation profiling.17
Third-Party Risk Management
While you strive to protect your city’s smarter infrastructure and network, it is important to protect it with outside “third parties” interacting with your ecosystem. This risk can pose a substantial threat surface to your otherwise well-protected ecosystem. Municipalities, especially smaller ones, often entrust their crown jewels—their residents’ data, their finances, their SCADA systems, and their business platforms—to third-party vendors they trust. However, a breach of your trusted third party often leads to a breach of your ecosystem as a result of credential compromise (stolen secrets). If you don’t think third-party risk is real, we would remind you that the now-famous Target breach was all due to a third-party vendor’s vulnerability. Currently the global IT managed service provider (MSP) giant Cognizant is facing an evolved Maze malware attack that has not only demanded ransom for encrypting data, but stolen a copy of the data as well.18 This emphasizes that while many MSPs offer IT expertise and services as valued partners, few are cyber experts.19
Third-party risk management (TPRM), the process of holding enterprises accountable to verifiable best practice standards, is difficult in a “verify then trust” world.20 Third-party verification is not asking the third party to answer a series of questions. Self-assessments and questionnaires are unreliable and suspect. MSPs need to have their infrastructure secured by an independent cybersecurity firm and present documentation to that effect. TPRM is about having an independent assessment and on-going monitoring of behaviors. This will not only protect your locality, but your vendors as well. TPRM requires deep optics, transparency, strong accountability, and effective collaboration. Achieving effective risk outcomes takes innovation requiring automated risk assessment capabilities informing meaningful cybersecurity management actions and metrics.
Your Weakest or Strongest Link?
In cybersecurity, your weakest and strongest links have something in common—they are your employees. Those who are haphazard are the weakest link and put even leading-edge technology at risk. Every CSF master plan must include employee cyber education. Training must be completed semi-annually with education across the board, including the city council, leadership team, staff, and even residents. Education needs reinforcement with periodic phishing campaigns to help determine compliance and effectiveness of your cyber standards. Developing a quality cyber culture through teaching precaution and awareness (not paranoia) will take time, but proper education policies and practices will help transform your city into a smarter city.
Call to Action
It is important for you to ask a lot of questions and seek out proven experts with proven methodologies. Local government leaders should ask three questions for focusing departmental risk discussions:
1. Are our identities and access privileges protected with best practices?
2. Are our confidential information and data encrypted at rest and in motion?
3. Were our operational control systems implemented with best practices and granular network segmentation?
If any of these questions are not clearly answered with fact-based detail, you have reason for concern. This can then lead to dialogue and vision clarification about how your city is protected in a smarter city architecture. Build your city’s vision, get a cyber assessment, and help develop and execute your cybersecurity first master plan. Follow up that effort with third-party cyber verification and validation. With a “verify then trust” culture evolving within your ecosystem, you can link vision to execution and become a smarter city.
© Copyright 2020 by Barry L. Schalkle, JD, CPA and Cyrus Olsen, PhD


Endnotes and Resources
1 Technologically, the smart city environment is a “zero-trust” ecosystem for a city. “Zero-trust” was originally coined by the Forrester group’s John Kindervag in 2010. It assumes that no digital infrastructure is safe, but is presumed to be vulnerable. It has evolved into a model where every single access request—whether it be made by a client in a coffee shop or a server in a datacenter—is rigorously checked or proven to be authorized (Zero Trust Networks, 2017, Gilman & Barth, O’Reilly Media Inc.) Here, in a smart city context, it includes IOT, IIOT, ICS, and data integration technologies under the city responsibilities as digital infrastructures. It is exposed to compromise from within and outside City IT boundaries by interactions with external and internal data and protocols.
2 Adapted from in NIST.SP.800-207-draft2, https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207-draft2.pdf, Zero Trust Architecture, Feb. 2020, p. 1.
3 New York Times, Aug 22, 2019, Updated Aug. 23, 2019. https://www.nytimes.com/2019/08/22/us/ransomware-attacks-hacking.html. In addition, in 2019, CNN reported that “targeted ransomware attacks on local U.S. government entities—cities, police stations, and schools—are on the rise, costing localities millions as some pay off the perpetrators in an effort to untangle themselves and restore vital systems.” https://www.cnn.com/2019/05/10/politics/ransomware-attacks-us-cities/index.html
4 https://blog.barracuda.com/2019/08/28/threat-spotlight-government-ransomware-attacks/
5 Jeff Kosseff, assistant professor of cybersecurity law at the U.S. Naval Academy, stated, “Municipal governments and hospitals…just don’t have the top cybersecurity out there, and the criminals know this.” He added, “You can see loss of life happening if the hospitals are not able to function. What terrifies me is if it happens on a large scale,” https://www.pure.si/cryptocurency/all-we-know-is-money-us-cities-struggle-to-fight-hackers/
6 Cyber risk management is not the elimination of risk in a zero-trust world, but the process of reducing uncertainty to a manageable and acceptable level within the scope of available resources.
7 https://securityboulevard.com/2018/ 07/survey-finds-breach-discovery-takes-an-average-197-days/
8 Michael Hayden and Richard Clarke on Greatest Cyberthreats facing America, https://www.youtube.com/watch?v=FdiAQBXGsMg
9 This is the reason National Institute of Standards and Technology generated the Cybersecurity Framework in 2014 with the latest updated version Draft NIST.IR.8183r1-draft, available at https://nvlpubs.nist.gov/nistpubs/ir/2020/NIST.IR.8183r1-draft.pdf for manufacturing environment risks. This framework identifies five core areas: identify, protect, detect, respond, recover, to drive an operational cybersecurity culture.
10 A smarter city threat surface is porous by design due to necessary integration of Internet of things (IOT), Industry 4.0 IOT (IIOT), industrial control systems (ICSs), services integration with vendors, digital transformation technologies like machine learning (ML) and artificial intelligence (AI), serverless container services, not to mention the data and platforms needed to provide advanced analytics and reporting.
11 ISC2 ’s 2019 survey of cybersecurity worldwide. It predicts a shortage of ~500,000 in the U.S. alone. (LATAM: ~600,000, Europe: ~291,000, APAC ~ 2.6M.) https://www.isc2.org/-/media/ISC2/Research/2019-Cybersecurity-Workforce-Study/ISC2-Cybersecurity-Workforce-Study-2019.ashx?la=en&hash=D087F6468B4991E0BEFFC017BC1ADF59CD5A2EF7
12 The POP TOP™ methodology is a model used by Cyber Security Warriors and has been applied to large organizations and city departments for intelligent infrastructure planning.
13 This can be the CISO role but must be protected from becoming merely operational as well. This role is the eyes, ears, and heart of the local government leader across departmental smart city interests and needs to be skilled in technology as well as management arts.
14 A “vector” has both magnitude and direction. These vision vectors first create a target and a magnitude of investments, as well as a directional guide for matrixed execution planning.
15 The local government leader owns responsibility for satisfying all stakeholders, and in the age of increasing surveillance fears, technology may be the least of their worries. Details on how you do this are in part 2, scheduled for July.
16 This can be controversial, but separation of duties of the cyber role from the IT role is critical for proper risk management. The IT role instantiates technical capabilities for least privilege, multifactor authentication, etc., and the cybersecurity role drives policy, compliance, awareness, and threat management with data and standards ensuring smarter city risk decisions are clear and managed across individual department optics.
17 Critical technical elements like secret and key management, identity access management (IAM), potential kill chains, surveillance standards and limitations, and other elements of cybersecurity as a discipline need to be thoughtfully digested with fact-based data to build out actionable remediation roadmaps in conjunction with technical roadmaps. These take the form of infrastructure challenges such as the need for sensor placements, telemetry integration, and other smart city considerations implied by a smarter city evolution.
19 IT services performed by third-party managed service providers (MSPs) need to have their infrastructure validated by an independent cybersecurity firm, and present attestations for city services security in smarter city architectures.
20 Ronald Reagan popularized the “trust but verify” motto; however, in a zero-trust world, it is inverted. Until verification is visible, trust cannot be given. Only with verified identity and validated authorization as least privilege policy can access be granted.
New, Reduced Membership Dues
A new, reduced dues rate is available for CAOs/ACAOs, along with additional discounts for those in smaller communities, has been implemented. Learn more and be sure to join or renew today!
